
October 1, 2018
Below are the top 3 phishing scams that Information Security has seen on campus so far this year.
- Office365 and OneDrive Scams
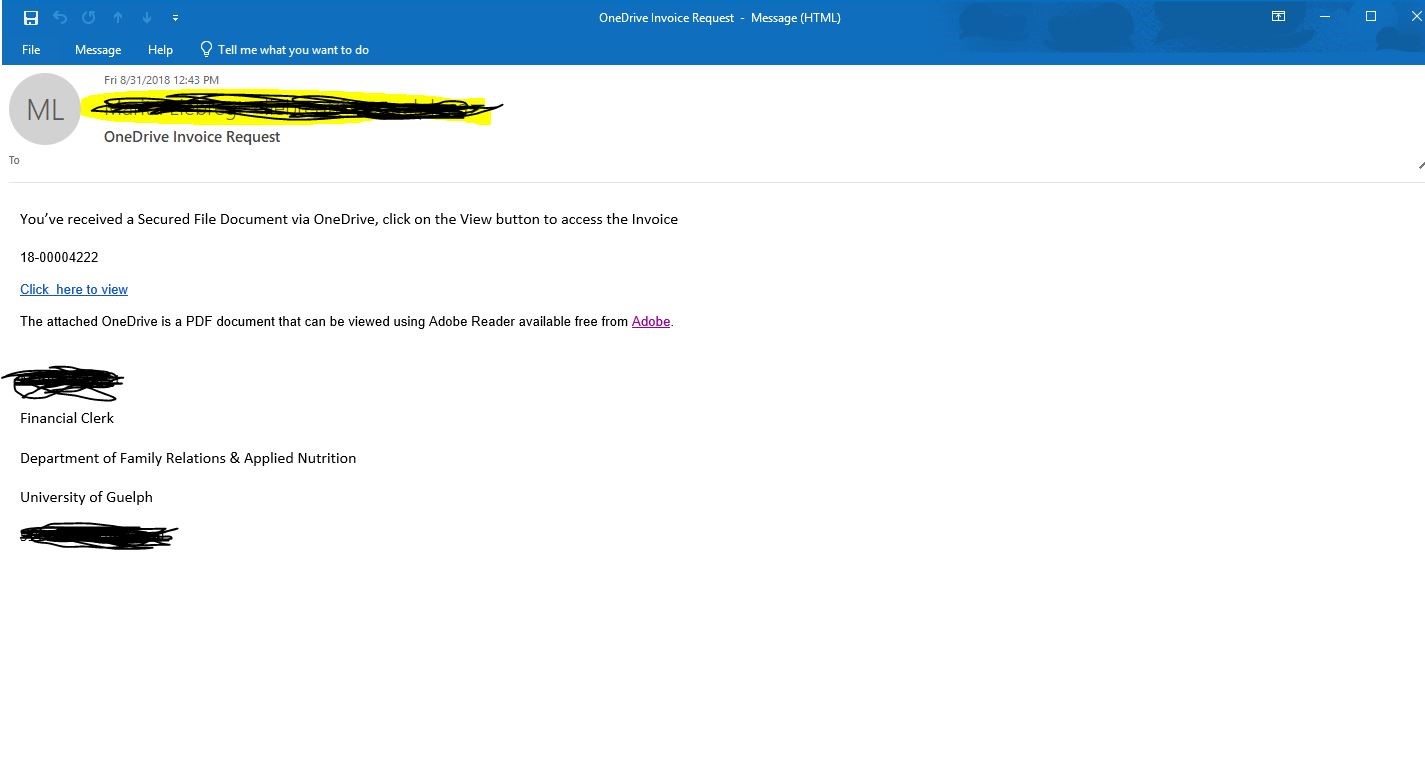
The deployment of Office365 and the OneDrive file sharing service on campus has made file sharing more efficient for everyone. However, it has also made it a prime attack vector for phishers because of the normality of receiving unexpected documents. In this phishing sample, a victim is asked to login into OneDrive in order to view an invoice by clicking on the link. If the targeted user clicks the link and enters their credentials, the phisher now has the victim’s credentials and full access to their account.
- Account Verification and Tech Support Scams
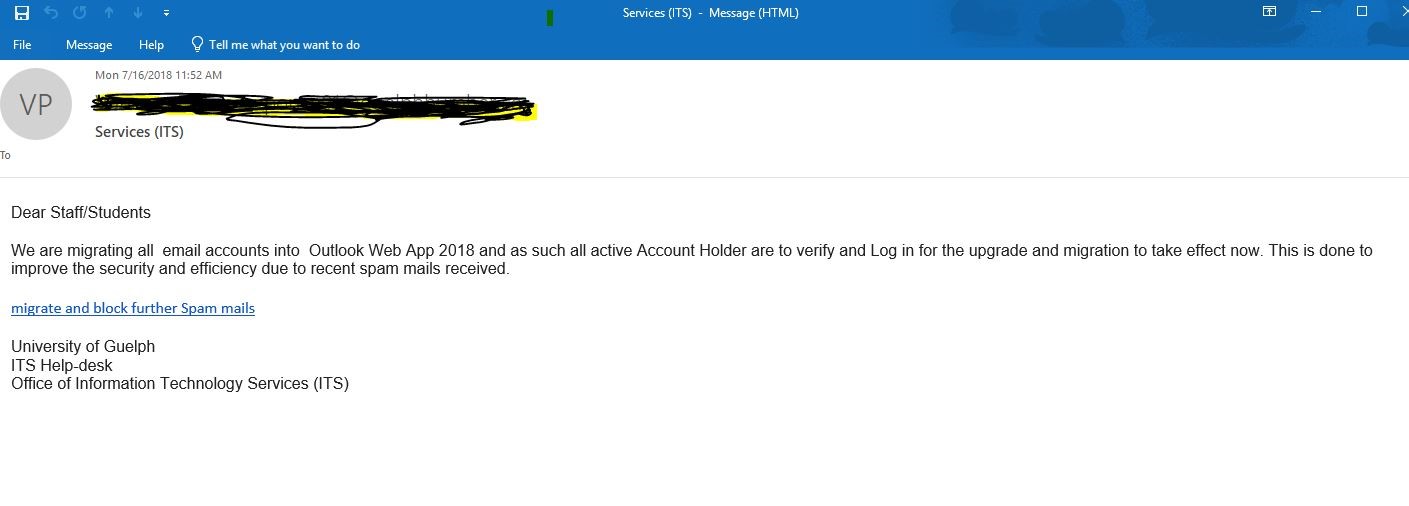
Tech support and account verification scams have been the most common type of phishing scam in recent years. In this scheme, users receive an email that appear to come from the University IT support team or from a well known company, such as Apple, Netflix or Amazon. The email states that there is a serious issue with your account and you need to sign in to correct it immediately. The attacker then steals your account credentials after you follow the instructions and login to the site they provide.
- CEO Fraud Scams
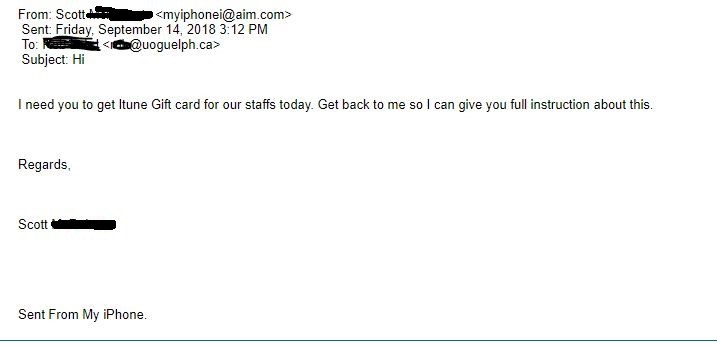
In a CEO Fraud scam, an attacker spoofs a message from your boss or an executive trying to trick you into wiring funds to fraudsters. In the example below, the phisher spoofed the director of a University department. If the employee replies to this message, they will be asked to purchase gift cards, scratch off the label on the back of the card to reveal the hidden security code, and then email pictures of the cards. With all that information the phisher can claim the value of those cards.
Written by: Hanna Guan (Cyber Security Analyst, Information Security)